Cybercriminals are always on the lookout for the next loophole to exploit. Given blockchain’s decentralized nature and ever-heightened cybersecurity defences, their target has shifted to the user data instead—a prime entry point for broader cybercrimes. To accomplish this, cybercriminals rely on common deceptive techniques known as spoofing and phishing.
What are spoofing and phishing?
Spoofing and phishing refer to the practices of disguising harmful content as legitimate communications from official sources. These techniques operate in one of two ways:
-
To trick users into revealing their important information and credentials, giving malicious parties access to their digital assets.
-
To impersonate official sources in an elaborate scam so that users give their digital assets away by their own will.
Both tactics involve psychological manipulation and system vulnerabilities. After all, it is certainly much more convenient for bad actors to mine the targets’ personal data for access rather than brute force their way into an airtight security system. Therefore, understanding and recognizing how spoofing and phishing work in various cryptocurrency scams is crucial to keep your information and assets secure.
Types of Cryptocurrency Scams
Scenario 1: Fake Bybit TR Website or Scam App with Fake Bybit TR Support
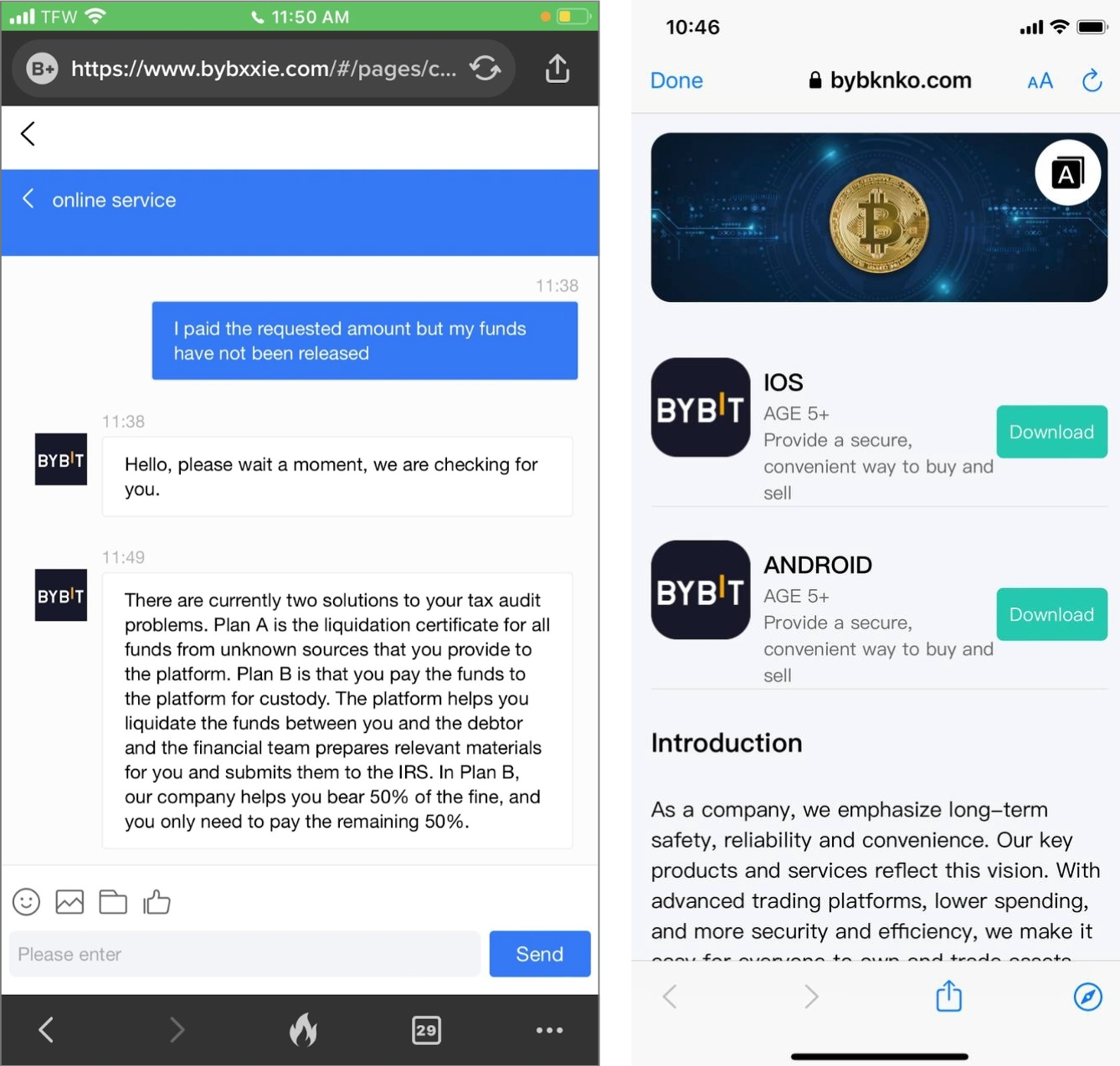
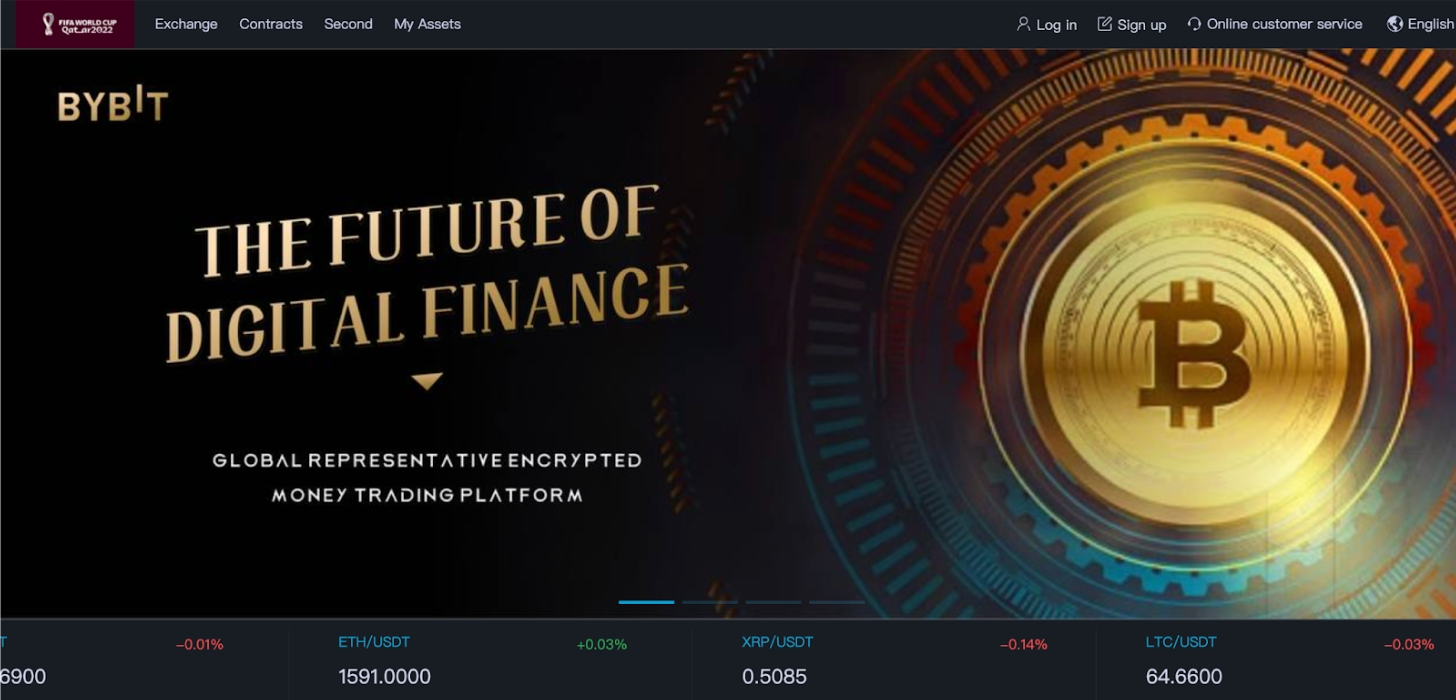
Scammers sometimes lure users by redirecting them to fake crypto trading platforms or digital wallets. These fake sites either work as phishing pages, which steal users’ private information, or offer fake services that appear as legitimate investment opportunities.
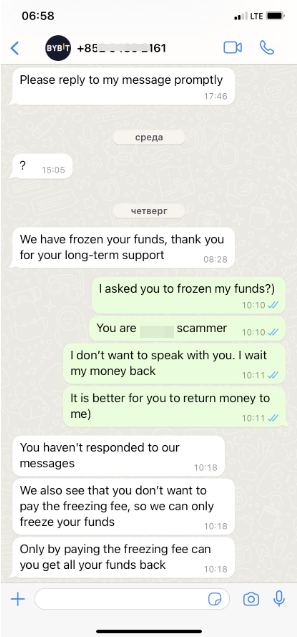
Scenario 2: Impersonating Bybit TR Official Staff to Contact Users
-
Individuals who are not official Bybit TR staff but act as Customer Support to contact users via social media such as Telegram, WhatsApp, X (formerly Twitter), or more.
-
Never share personal details, such as passwords, bank accounts, or wallet information, with unverified sources.
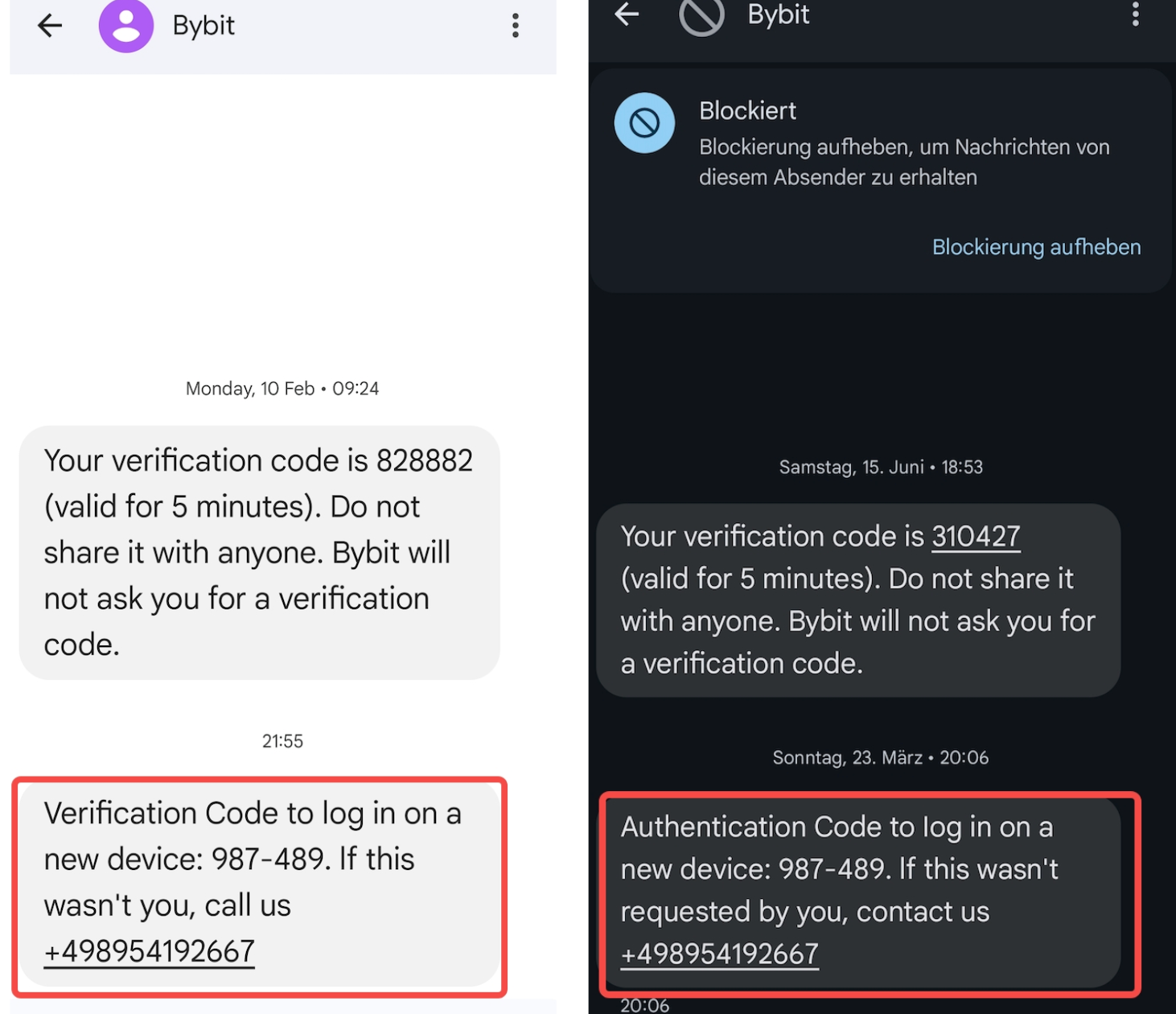
Scenario 3: Fake Bybit TR SMS Scam Alert
We have detected a phishing scam where fraudsters send fake SMS messages to random users. These messages often claim that if the verification code was not requested by the user, they should call a provided phone number.
In an attempt to appear as legitimate communication, the schemes sometimes use fake sender IDs to mask the original senders in the SMS header. This means that these deceptive texts may even show up in the same conversation thread as previous Bybit TR’s official messages.
Please be advised:
Bybit TR will never provide or request users to contact any phone number. We do not offer customer support via hotline calls and will never send SMS messages containing links (URLs), requests to contact customer service, or instructions to make phone calls.
Please remain vigilant and do not trust any suspicious calls or text messages claiming to be from Bybit TR. Always verify information through Bybit TR’s official channels.
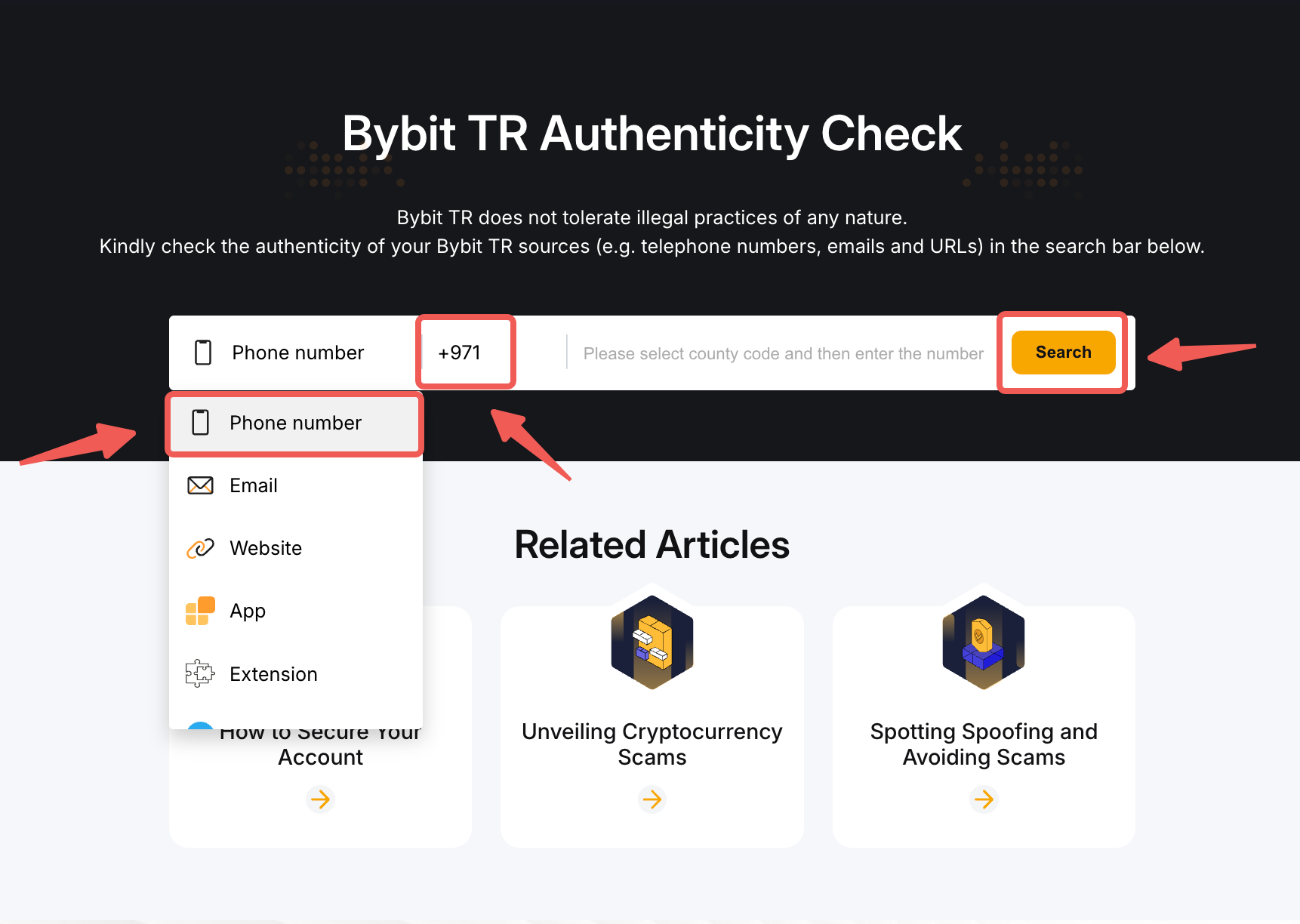
Solution
In the event that you receive an SMS scam alert, we strongly recommend that you block the suspicious or unknown number to prevent receiving further scam messages.
For Android users:
Step 1: Open the Phone app.
Step 2: Tap the three-dot menu in the upper-right corner and select Settings.
Step 3: Choose Block numbers or Block and report spam.
For iPhone (iOS) users:
Step 1: Open the text message from the number you want to block.
Step 2: Tap the sender’s number, then tap the info (i) icon.
Step 3: Select Block this Caller → Block Contact.
For more information on how to protect yourself from phishing text messages, please refer to the Prevention Tips.
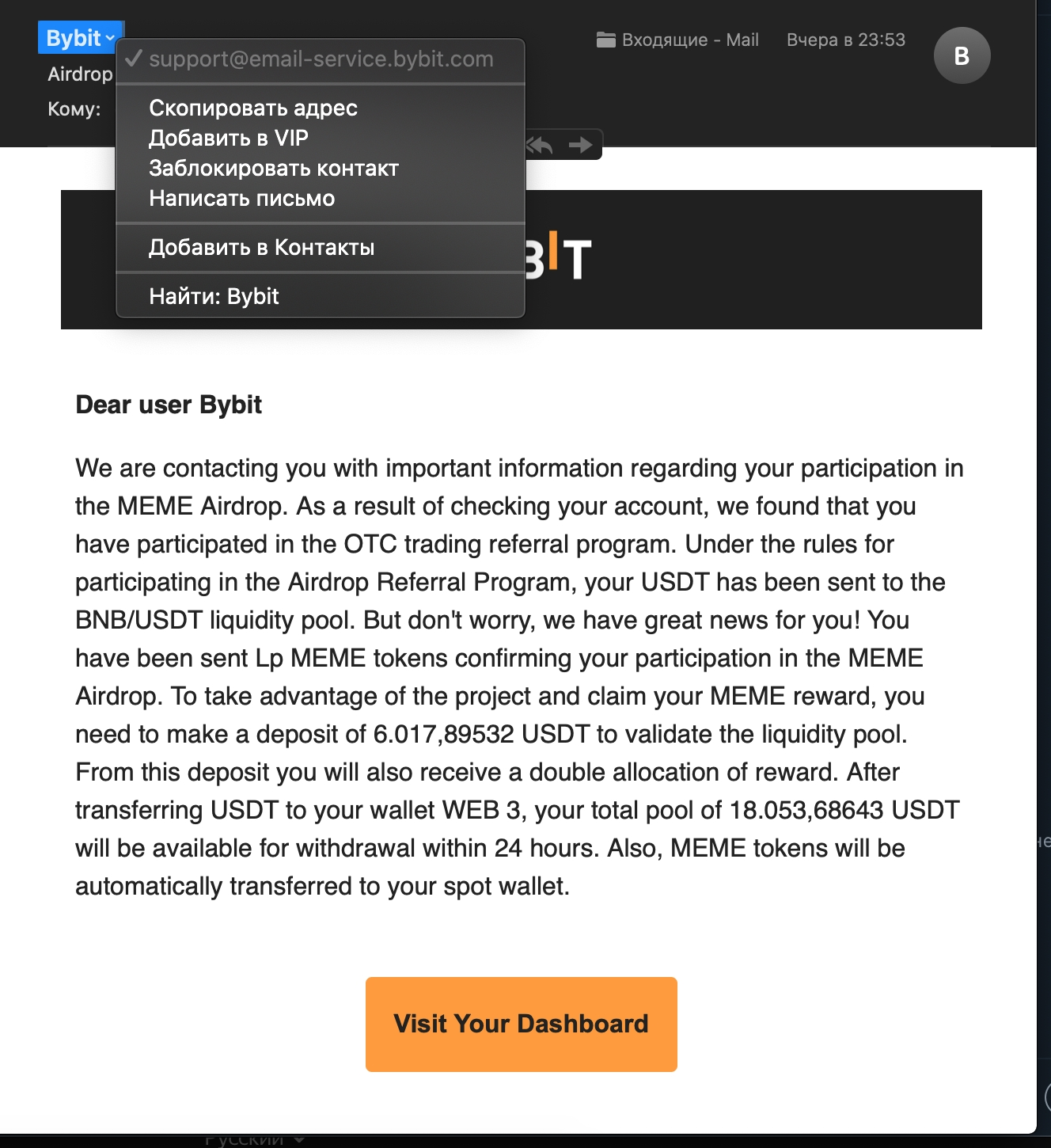
Scenario 4: Fake Airdrop or Rewards
-
The common tactic is to persuade users to transfer a certain amount to an unknown deposit address to claim an airdrop or reward.
-
Always be cautious of promotions that seem too good to be true, and verify suspicious messages or offers by contacting Bybit TR’s official support.
Scenario 5: Impersonating Bybit TR Social Media Account
-
Always look for verification badges, review profile details, and compare with the official website.
-
Bybit TR does not use any WhatsApp channels to communicate. Any WhatsApp group or message claiming to be from Bybit TR is fraudulent.
|
Fake Account |
Official Account |
|
|
|
You can visit Bybit TR’s official social media channels via the quick links located at the footer of the Bybit TR website.
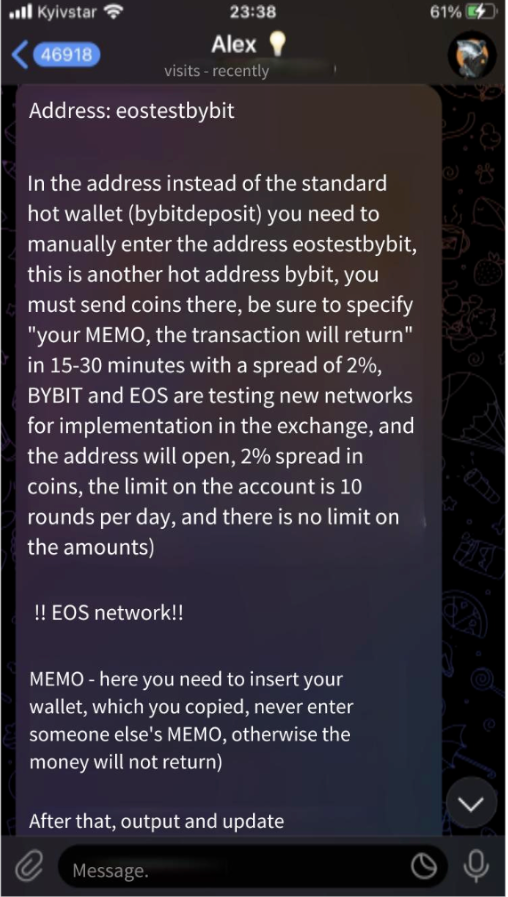
Scenario 6: Ask Users to Transfer Funds to Fake Bybit TR Wallet Address
-
This scam involves scammers deceiving users by claiming that Bybit TR is currently collaborating with certain token projects' developers to test the performance of the blockchain.
-
The scammers then provide detailed instructions on how users can deposit funds into their Bybit TR accounts, appearing helpful to lower users' guards.
-
Subsequently, they provide a withdrawal address bearing the Bybit TR name, falsely posing as an official address. Users are instructed to withdraw funds to this address under the guise of assisting with testing, promising a reward of X% of the withdrawn amount.
-
Initially, the scammers transfer rewards to users to lure them further. However, as the amount involved grows, the scammers disappear with the users' assets, leaving them unable to retrieve their funds.
Important:
As we have always emphasized, Bybit TR will never ask you to withdraw to unknown wallet addresses. It's a cautionary tale to always be wary of offers that seem too good to be true and to double-check before sending money anywhere.
In conclusion, staying vigilant and cautious when dealing with emails and online communications is essential in protecting oneself from falling victim to spoofing and phishing scams. By remaining aware of common tactics used by scammers and exercising diligence in verifying the authenticity of communications, you can better safeguard your assets and personal information in the crypto realm. To learn more about how to enhance the security of your account, please refer to here.